Damn! We are already on Post 2?😱😱😱
I guess I'm really doing this huh?😏😏😏
Aight! Let's Begin!
Understanding The Question
This is The Question.
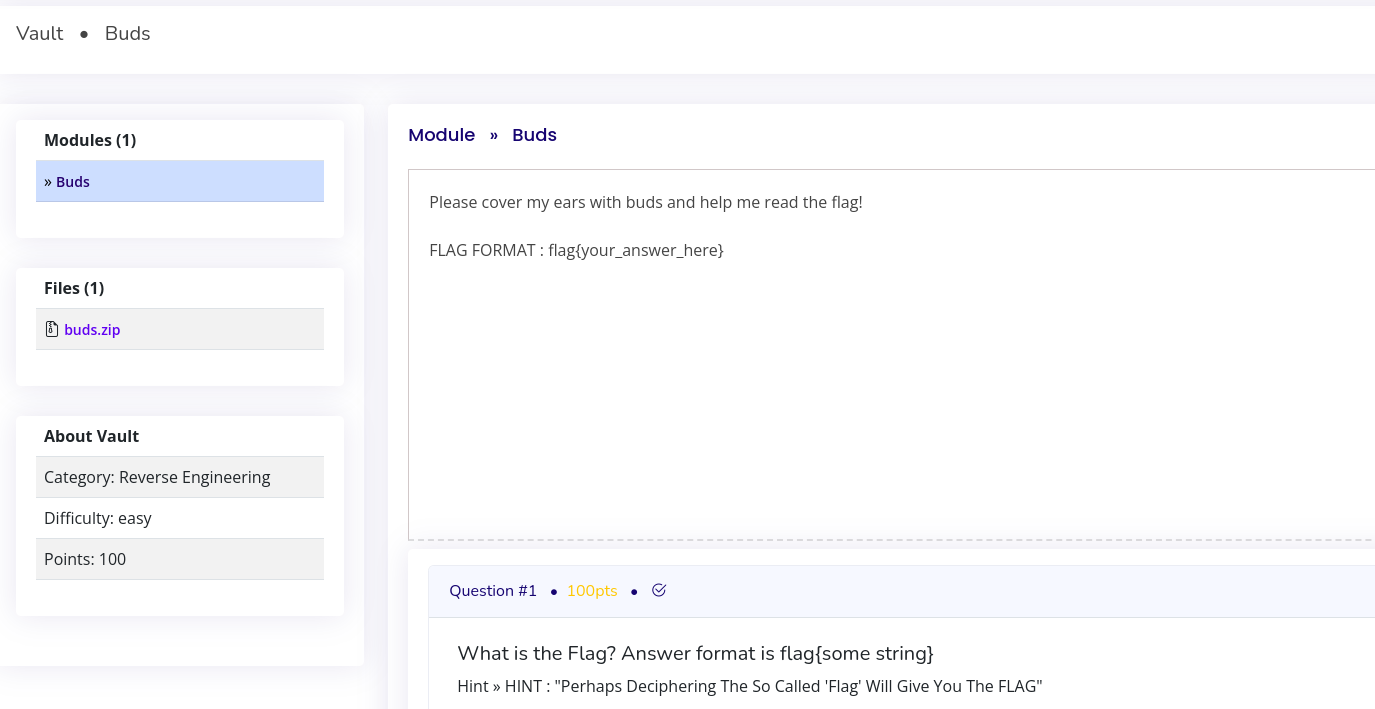 Screenshot of the "Buds" challenge question
Screenshot of the "Buds" challenge question
We can see the text :
Please cover my ears with buds and help me read the flag!
So this challenge has something to do with music
But we are also given a zip file which upon downloading and extracting we see:
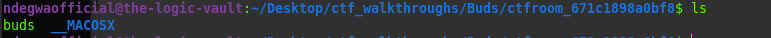 ls command on the extracted folder
ls command on the extracted folder
We can see the zip file contains a file called 'buds'
Let's identify what type of file this is
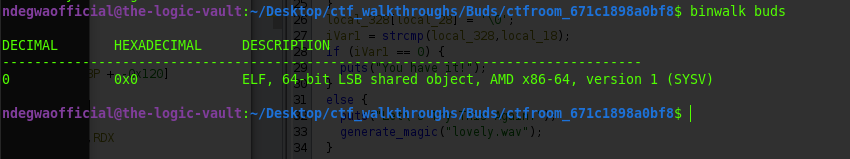 binwalk command on "buds" file
binwalk command on "buds" file
The binwalk tool tells us that "buds" file is an ELF format meaning it is an Executable and Linkable File Format
This tells us 2 things:
- We can interact with it by executing/running it
- That it is a binary file which we can reverse engineer and get the source code.
Let's start with 1
We first give executing permissions on the file, then we proceed to interact with the program and see
what it does.
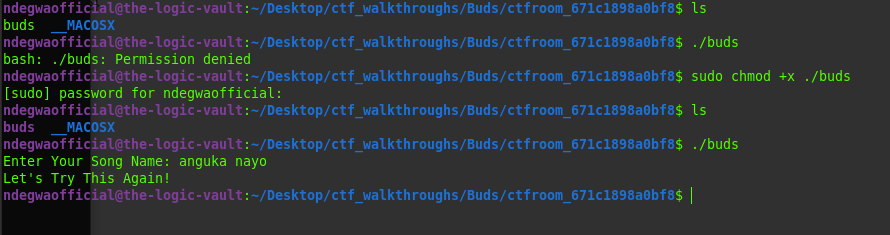 executing the buds program
executing the buds program
Well! pretty disappointing, but still useful.
The program asks us for a song name and seems to check for a specific song
So what next?
Method 2
We will need to call upon the mighty dragons From NSA, and see if they can help us out.
Yeah, that's right We will use Ghidra to disassemble our buds file and hopefully get the source code.
So I fired up Ghidra, created a project and imported the buds file.
After analysis, this was the source code for our point of interest: (The Main Function)
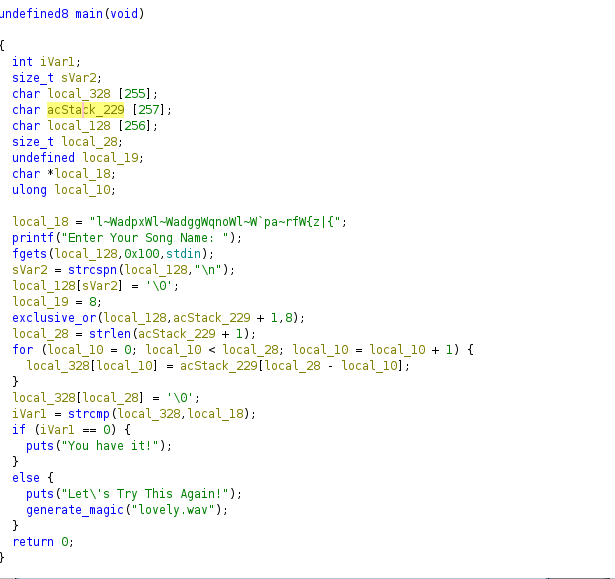 source code of the buds program
source code of the buds program
Understanding the source code
The program seems to prompt the user for a song name, then checks if it matches a specific hardcoded string and then generates a "lovely.wav" file if the song entered does not match.
Pretty weird right? Like who does that??????
Okay, Let's move on
The first point of interest is this weird string just before the printf statement
local_18 = "l~WadpxWl~WadggWqnoWl~W`pa~rfW{z|{";
We see this is what the program checks for, and if it doesn't match, it generates a lovely.wav file. But not that simple.
It reads the input into local_128 and removes the newline character
It then performs an XOR operation with the byte 8 of each character of the input string
Then Reverses the XORed string and compares it to the hardcoded weird string
l~WadpxWl~WadggWqnoWl~W`pa~rfW{z|{
If the input matches the string, it prints "You have it!"
Deciphering the String
I wrote a python script that helped me perform the XOR Operation with the byte 8, on the weird string
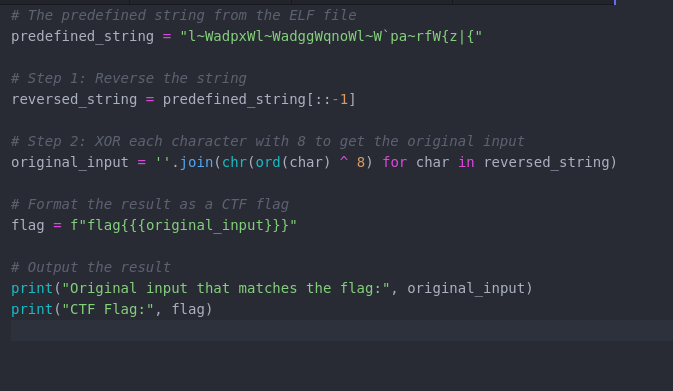 Python Script to XOR String
Python Script to XOR String
First I reversed the string then XORed each charachter to get the original input
Running the script returned this:
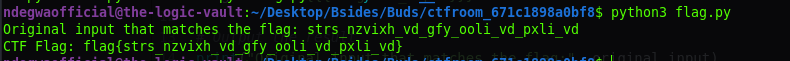 running the Python Script
running the Python Script
Pretty weird right?... It shows some kind of flag but we are definitely sure that this is not the expected flag.
Why?... Well, unless we started listening to K-POP music. It's not even remotely related to a song.
flag{strs_nzvixh_vd_gfy_ooli_vd_pxli_vd}
Remember this part of the question?.... That's right
Atleast we know we are on the right direction
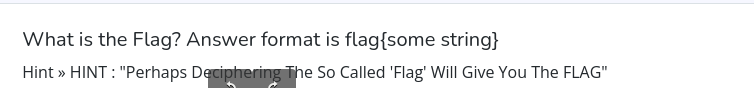 hint
hint
I tried deciphering the string strs_nzvixh_vd_gfy_ooli_vd_pxli_vd with ROT but it didn't work
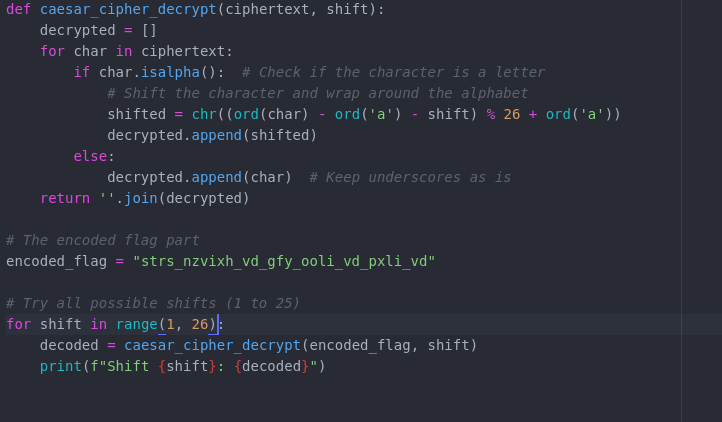 ROT Decipher Script
ROT Decipher Script
The Output was:
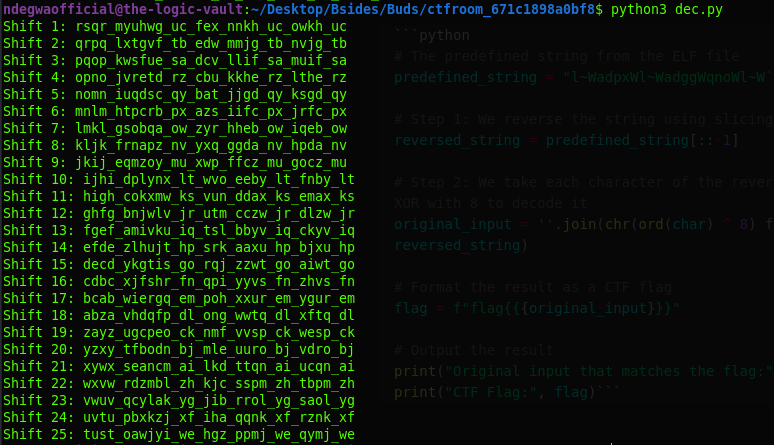 running the ROT Deciphering Script
running the ROT Deciphering Script
So The next course of action was deciphering with Atbash
Atbash Deciphering
Atbash is a simple substitution cipher that replaces each letter with the letter at the opposite end of the alphabet
E.g A becomes Z and B becomes Y... You gerrit? If you don't gerrit well....
I wrote a simple Atbash Deciphering Script
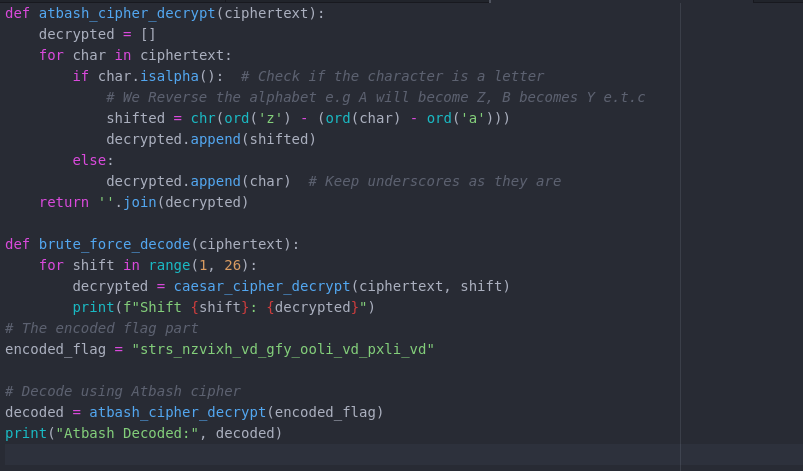 Atbash Deciphering
Atbash Deciphering
and upon running it, I got the output:
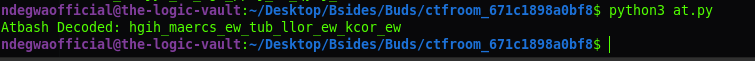 hint
hint
So we got this text:
hgih_maercs_ew_tub_llor_ew_kcor_ew
Let's Write it from the right to left
we_rock_we_roll_but_we_scream_high
Voila!... This actually makes sense!
And this is our flag:
flag{we_rock_we_roll_but_we_scream_high}
So, I guess that's it. I really don't know how to end this things. Amen?... Adios?
Adios seems good.
So, Adios Muchachos!
REMEMBER: Bsides Nairobi Challenge is happening this november and would really use you financial donations to help make the
event a success. You can donate here: Bsides Nairobi 2024

 Screenshot of the "Buds" challenge question
Screenshot of the "Buds" challenge question ls command on the extracted folder
ls command on the extracted folder binwalk command on "buds" file
binwalk command on "buds" file executing the buds program
executing the buds program source code of the buds program
source code of the buds program Python Script to XOR String
Python Script to XOR String running the Python Script
running the Python Script hint
hint ROT Decipher Script
ROT Decipher Script running the ROT Deciphering Script
running the ROT Deciphering Script Atbash Deciphering
Atbash Deciphering hint
hint