Post 3 already and I still can't find a proper intro...
Oh God, Winter is here.
Yes. The challenge creator goes by that name and indeed, when you are not shivering from the cold heart break his challenges will give you, you are contemplating on throwing your laptop in the freezer because it seems to be going bad.
This challenge is a Windows CTF challenge. The goal is to get the flag from the shared memory.
Aight! Let's Begin!
Understanding The Question
This is The Question.
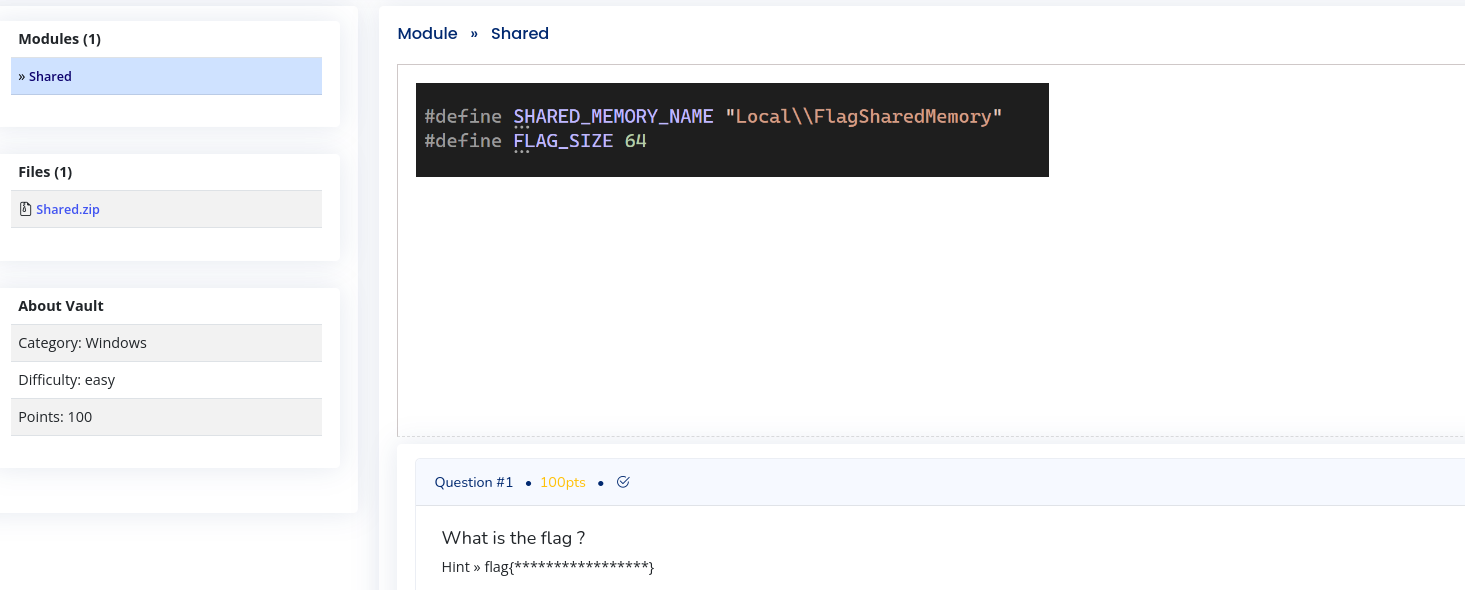 Screenshot of the "Shared" challenge question
Screenshot of the "Shared" challenge question
We can see the Code :
#define SHARED_MEMORY_NAME "Local\\FlagSharedMemory"
#define FLAG_SIZE 64
We have also been given a .zip file which contains a program "Shared.exe"
What does it mean?
Well The SHARED_MEMORY NAME sets the name of a shared memory region to Local\\FlagSharedMemory
This shows that this is where the flag we need to retrieve is stored by the program.
The FLAG_SIZE 64 is self explanatory, it sets the size of the shared memory to 64 bytes.
So, What Next?
Logically, Our first course of action will be running the Shared.exe and see the program in action
Since I use Linux, I will use Wine to run the program.
Wine adds a compatibility layer to allow Linux and MACOS Users run windows Programs
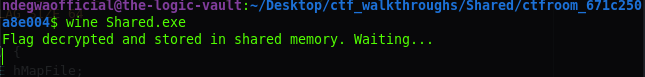 Running Shared.exe with Wine
Running Shared.exe with Wine
After running the program, it prints the text
Flag decrypted and stored in shared memory. Waiting...
This Means 2 Things:
- We can reverse engineer the program to see how it decrypts the flag, then get the encrypted flag and attempt to decrypt it ourselves or
- We can access the already decrypted flag that has been dumped on the Shared Memory.
We will go with method 2. Why? Well... It's Easier, and also, Based on the hints the challenge creator gave, it seems like the challenge creator wants to test our ability to gain access to shared memory.
Accessing Shared Memory
I decided to use C to write a small program to help me get access to the flag stored in the shared memory.
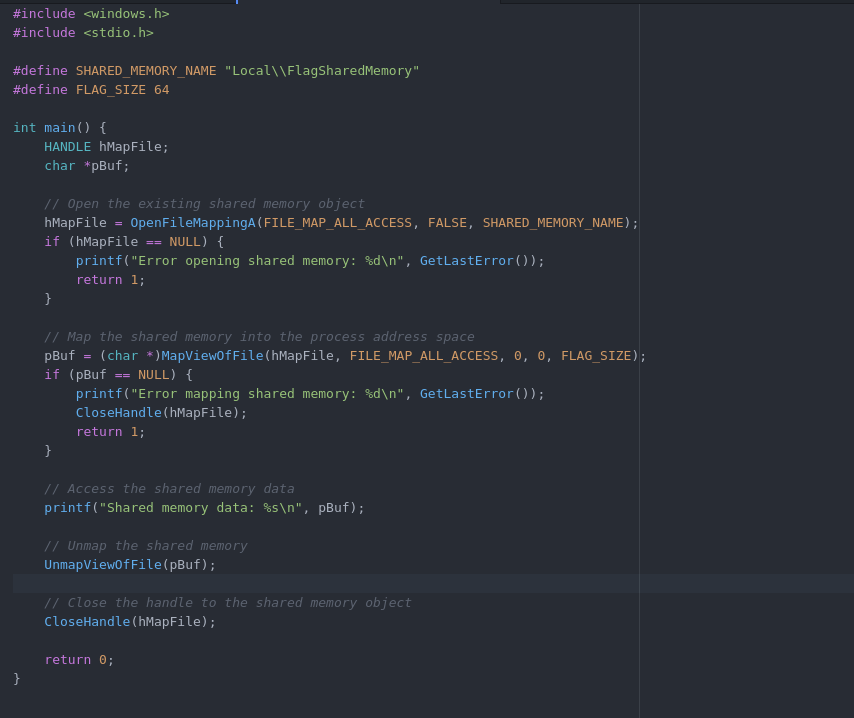 C Program to retrieve flag
C Program to retrieve flag
Let me explain why I used that Logic.
From our provided hints, we saw that the shared memory object is SHARED_MEMORY_NAME.
Therefore, I used the hMapFile = OpenFileMappingA(FILE_MAP_ALL_ACCESS, FALSE, SHARED_MEMORY_NAME); to open the shared memory object with full acsesss permissions. The FALSE Parameter simply means that we are not creating a shared memory, but opening an already existing one.
What follows is basic error handling
Then I mapped the shared memory object into the current process's (This C program) memory space using the MapViewOfFile function.
Those are the most important bits of our program.
So, Let's compile our program.
Compiling with the conventional GCC on linux will result in errors because our program calls Windows APIs with the #include <windows.h>. So I used x86_64-w64-mingw32-gcc Compiler accompanied with the -luser32 flag to tell the linker to include the "User32 library" which will provide access to the windows functions
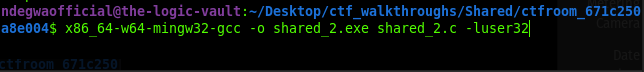 Compiling the Program
Compiling the Program
After Successfully Compiling, I ran the program with Wine and it printed the flag
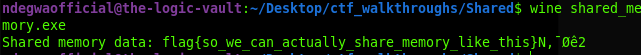 Retrieving The Flag
Retrieving The Flag
Here is the Flag:
flag{so_we_can_actually_share_memory_like_this}
So. Once again, We've reached my most dreaded moment.
I've ran out of creative ways to end these things. So, I'll just say that this was a fun challenge and I'm glad I could solve it.
See you on Shared2 which actually made me cry!!!
REMEMBER: Bsides Nairobi Challenge is happening this November and would really use you financial donations to help make the
event a success. You can donate here: Bsides Nairobi 2024

 Screenshot of the "Shared" challenge question
Screenshot of the "Shared" challenge question Running Shared.exe with Wine
Running Shared.exe with Wine C Program to retrieve flag
C Program to retrieve flag Compiling the Program
Compiling the Program Retrieving The Flag
Retrieving The Flag